Reinforces commitment to a safer internet
DUBAI, UAE, 24th June, 2025 – In mid-May 2025, Cloudflare blocked the largest DDoS attack ever recorded: a staggering 7.3 terabits per second (Tbps). This comes shortly after the publication of the company’s DDoS threat report for 2025 Q1 on April 27, 2025, where it highlighted attacks reaching 6.5 Tbps and 4.8 billion packets per second (pps).
The attack targeted a Cloudflare customer, a hosting provider, that uses Magic Transit to defend their IP network. Hosting providers and critical Internet infrastructure have increasingly become targets of DDoS attacks, as was reported in Cloudflare’s latest DDoS threat report.
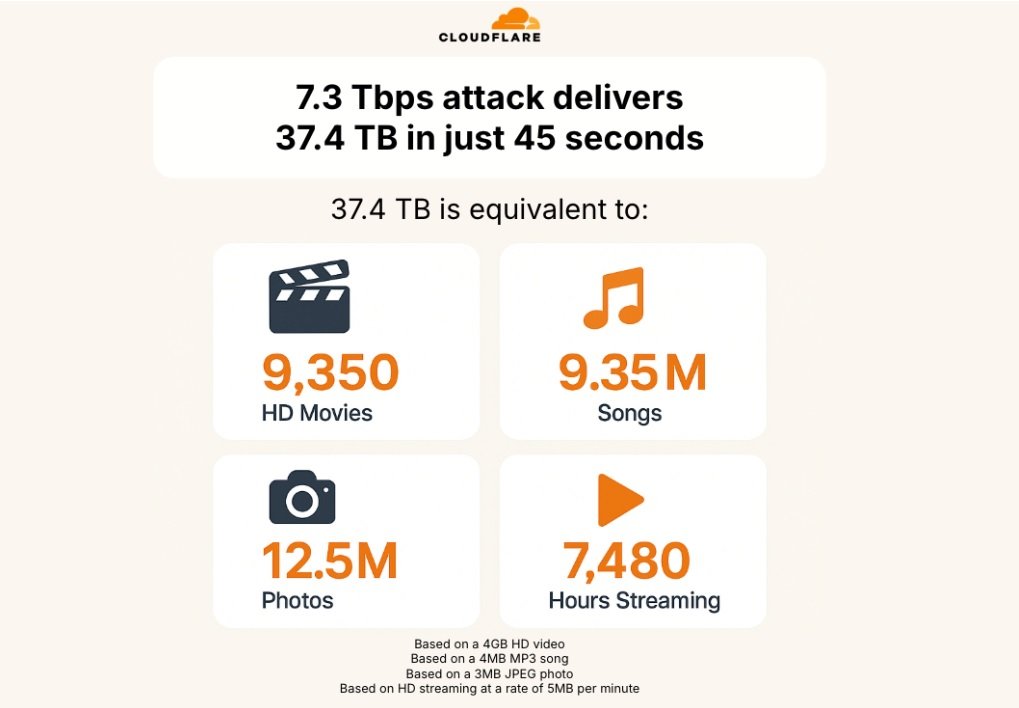
The 7.3 Tbps attack delivered 37.4 terabytes in 45 seconds
37.4 terabytes is not a staggering figure in today’s scales, but blasting 37.4 terabytes in just 45 seconds is. It’s the equivalent to flooding your network with over 9,350 full-length HD movies, or streaming 7,480 hours of high-definition video nonstop (that’s nearly a year of back-to-back binge-watching) in just 45 seconds. If it were music, you’d be downloading about 9.35 million songs in under a minute, enough to keep a listener busy for 57 years straight. Think of snapping 12.5 million high-resolution photos on your smartphone and never running out of storage—even if you took one shot every day, you’d be clicking away for 4,000 years — but in 45 seconds.
This attempted takedown was not just a technical anomaly—it was a serious threat to the stability of the digital world. Cloudflare’s advanced protection systems automatically detected and neutralized the massive wave of malicious traffic in real time, without any disruption to the targeted services.
The attack used a newly emerging technique, which exploited a weakness in HTTP/2, a commonly used web protocol. What made it particularly dangerous was its speed and scale. The attacker tried to send over 200 million requests per second, a level of traffic designed to cripple even the most robust infrastructure.
The attack details
The attack carpet-bombed an average of 21,925 destination ports of a single IP address owned and used by our customer, with a peak of 34,517 destination ports per second. The attack also originated from a similar distribution of source ports.
Attack vectors
The 7.3 Tbps attack was a multivector DDoS attack. Around 99.996% of the attack traffic was categorized as UDP floods. However, the remaining 0.004%, which accounted for 1.3 GB of the attack traffic, were identified as QOTD reflection attacks, Echo reflection attack, NTP reflection attack, Mirai UDP flood attack, Portmap flood, and RIPv1 amplification attacks.
Attack origins
The attack originated from over 122,145 source IP addresses spanning 5,433 Autonomous Systems (AS) across 161 countries.
Almost half of the attack traffic originated from Brazil and Vietnam, with approximately a quarter each. Another third, in aggregate, originated from Taiwan, China, Indonesia, Ukraine, Ecuador, Thailand, the United States, and Saudi Arabia.
Free botnet threat feed
To help hosting providers, cloud computing providers, and any Internet service providers identify and take down the abusive accounts that launch these attacks, Cloudflare leverages its unique vantage point to provide a free DDoS Botnet Threat Feed for Service Providers. Over 600 organizations worldwide have already signed up for this feed. It gives service providers a list of offending IP addresses from within their ASN that we see launching HTTP DDoS attacks. It’s completely free and all it takes is opening a free Cloudflare account, authenticating the ASN via PeeringDB, and then fetching the feed via API.
Protecting the Internet
Cloudflare’s systems successfully blocked this record-breaking 7.3 Tbps DDoS attack fully autonomously without requiring any human intervention, without triggering any alerts, and without causing any incidents. This demonstrates the effectiveness of the company’s world-leading DDoS protection systems. It built this system as part of its mission to help build a better Internet committed to provide free unmetered DDoS protection.
Cloudflare’s ability to block such a monumental attack showcases the strength of its global network, which spans more than 300 cities in over 100 countries. The company’s automated systems, built with resilience and speed in mind, ensure that even the most aggressive cyber threats are swiftly neutralized.
As the digital world continues to grow, so do the threats against it. Cloudflare remains committed to staying ahead of cybercriminals and providing protection that’s always on, always learning, and always ready.
To read more about the attack and how it was mitigated, visit the official blog post here: https://blog.cloudflare.com/defending-the-internet-how-cloudflare-blocked-a-monumental-7-3-tbps-ddos
-Ends-
About Cloudflare
Cloudflare, Inc. (NYSE: NET) is the leading connectivity cloud company on a mission to help build a better Internet. It empowers organizations to make their employees, applications and networks faster and more secure everywhere, while reducing complexity and cost. Cloudflare’s connectivity cloud delivers the most full-featured, unified platform of cloud-native products and developer tools, so any organization can gain the control they need to work, develop, and accelerate their business.
Powered by one of the world’s largest and most interconnected networks, Cloudflare blocks billions of threats online for its customers every day. It is trusted by millions of organizations – from the largest brands to entrepreneurs and small businesses to nonprofits, humanitarian groups, and governments across the globe. Learn more about Cloudflare’s connectivity cloud at cloudflare.com/connectivity-cloud. Learn more about the latest Internet trends and insights at https://radar.cloudflare.com.